The idea of a computer program as a salable artifact that one purchases like one would a book or record album was still quite a new one in 1978. In the world of institutional computing, commercial software was largely confined to operating systems and the most complicated, critical applications such as compilers, and was created and sold by the same companies that produced the hardware on which it ran; TOPS-10 was a product of DEC itself, Time-Shared BASIC a product of Hewlett-Packard, etc. These programs were sold not as individual products with fixed price tags, but rather negotiated as part of complicated contracts that also involved the hardware to run them and the personnel to support them. Software created by end-users of these machines was often so specialized as to be useless outside of the site where it was created, and where this was not the case was distributed freely. Since there was no real commercial market for stand-alone software, there was no incentive to do anything else.
That began to change virtually from the moment that the microcomputer age began. The first piece of standalone microcomputer commercial software was created by the company that would (for better or for worse) become synonymous with the closed-source commercial model of software distribution: Microsoft. That company’s first product, created in 1975 while Bill Gates and Paul Allen were still scruffy university students, was a version of BASIC sold on paper tape for the Altair 8800 kit computer. On February 3, 1976, Gates sent an “open letter to hobbyists” that has since become famous. In it he derided the widespread copying of Microsoft’s software, noting that, while seemingly every Altair owner was using BASIC, fewer than 10% had actually bought it, and claiming that he and Allen’s financial reward for their time spent developing it amounted to less than $2.00 per hour. Hobbyists reacted to the letter with surprise and a fair amount of outrage. It’s probably fair to say that the concept of software that was not freely distributable, and thus the very idea of software “piracy,” had never occurred to them, so antithetical was it to the ethos of sharing and open information exchange of places like the Homebrew Computer Club. One Jim Warren replied:
There is a valid alternative to the problems raised by Bill Gates in his irate letter to computer hobbyists concerning “ripping off” software. When software is free, or so inexpensive that it’s easier to pay for it than to duplicate it, then it won’t be “stolen.”
Note the use of quotations around “ripping off” and “stolen,” as if these concepts in relation to software are farcical. The debate touched off by Gates and Warren still rages to this day. It’s also a morass I know better than to wade into here. Suffice to say that after Altair BASIC the proverbial cat was out of the bag, and software distribution was changed forever.
As I noted in an earlier post, Radio Shack was wise enough to realize that good software support was very important to the success of its new computer (an obvious fact that Commodore, among others, never seemed to fully grasp). Since almost all TRS-80s were sold from Radio Shack stores, the company had a great opportunity to create that support by encouraging submissions from hobbyists programmers and selling the best right alongside the computers themselves. It’s therefore kind of odd that most of the best and most interesting TRS-80 programs were not published by Radio Shack. Presumably the drawbacks of dealing with a huge, faceless corporation’s acquisitions department outweighed the distribution advantages.
The main facilitator of software distribution in this era was instead rather surprising: the magazines. Creative Computing had of course been publishing program listings in BASIC for years before the arrival of the TRS-80 and its competitors, and continued to do so now. And with an October, 1978, issue SoftSide magazine, the first TRS-80-specific magazine and I believe the first platform-specific magazine of any stripe, began publication with this mission statement:
Our intention is to publish software — and lots of it, free for the transcription. Every month we will offer programs for business, games, programs with household applications, even educational programs for children that will allow your home computer to become the educational aid we always knew it could be. Our content will be as diverse and unique as our featured programs’ writers.
Of course, that “transcription” made for one hell of a pain; laboriously typing in the hundreds of lines of code for some of the surprisingly complex programs that SoftSide published was No Fun, no matter how enamored you were with your new computer — and that’s not even considering the subtle bugs that could be introduced by getting a letter or a digit wrong here or there. Therefore SoftSide also sold an optional accompanying cassette for each issue, which contained all the programs published therein.
But that was only the beginning. Even before the birth of the magazine, SoftSide‘s publishers had formed The TRS-80 Software Exchange as a distribution organ for commercial software. In fact, the cynical might say that they formed Softside largely to promote TSE; each issue devoted a considerable number of pages to catalog listings of TSE’s titles, with the most commercially promising also being accorded individual half- or full-page spreads. In a sense, TSE was one of the first software publishers — but only in a sense. Publishing with TSE carried an advantage developers would kill for today:
You retain the rights to the programs you worked so hard to write. If your programs don’t sell, you don’t make money, so why tie up your software with an exclusive contract? With SoftSide, you’re free to market through us, and still sell your programs privately or through other non-exclusive arrangements. We prefer to let our performance be the only “tie that binds.”
What a deal, eh? No wonder so many hobbyists programmers desperate to get their programs into the hands of the masses and earn a little scratch along the way rushed to send in their creations. Scott Adams was among them; even before coding Adventureland he released a “3D tic-tac-toe” and a backgammon game through TSE. And like many others, he took full advantage of TSE’s generous terms by releasing as well through Creative Computing Software, a similar organ set up by that magazine, and also by selling what he could on his own. (For some fun anecdotes about what that was like, check out Matt Barton’s interview with Adams.) All of this occurred fully a year before Adams founded Adventure International, a real software publisher of his own. Adventureland first appeared in SoftSide‘s January, 1979, issue, being sold for $24.95 in tandem with a second adventure Scott had already written by that time with his then-wife, Alexis. Called Pirate Adventure, this game is both easier and more fondly remembered by most players than Adventureland itself.
It’s amusing to look back today on how naive and clumsy the early commercial game market was. Adams and TSE can’t even seem to settle on a name. In addition to its (presumably) real name, Adventureland appears in TSE advertisements as simply Adventure (now that’s a recipe for confusion!) or, my favorite, the evocative and enticing Land Adventure. (Well, I guess it’s factually accurate…) The second game, meanwhile, vacillates among Pirate Adventure, Pirate’s Adventure, and Pirate’s Cove.
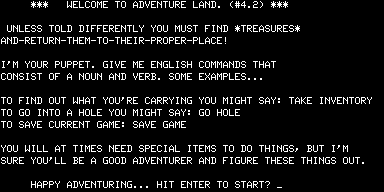
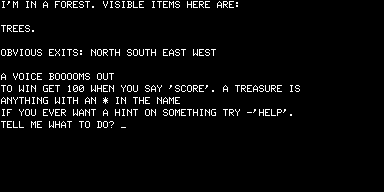
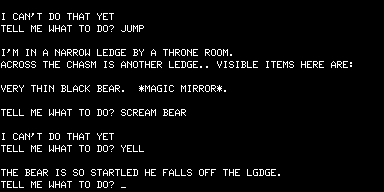
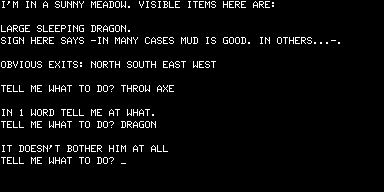
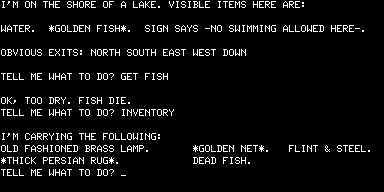
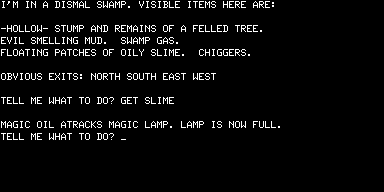
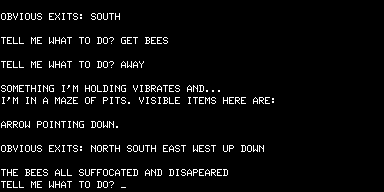
But none of that mattered a jot. Adams’s adventures were absolutely unique, and they were being sold into a growing market hungry for interesting and entertaining new games. Most TRS-80 owners had no access to the large institutional machines that ran the original Adventure, making Adams’s games their first exposure to the form, the bridge that brought the innovations of Crowther and Woods to the burgeoning world of home computing. Like all those PDP-10 hackers, once they had solved Adams’s games many TRS-80 programmers started thinking about how to create their own. And so a genre was well and truly born.